
Verifiable compute is rapidly emerging as the backbone of next-generation crypto infrastructure, unlocking a new era of trust-minimized, scalable, and AI-ready applications. At DAS London, Eigen Labs’ J. T. Rose captured the industry’s imagination by pitching verifiable off-chain compute with agentic AI coming to Ethereum. The message was clear: the future of crypto infra lies in making even the most complex off-chain computation as provable and trustworthy as a smart contract execution.

Why Verifiable Compute Is a Game Changer
Traditional blockchain apps have been boxed in by the limitations of on-chain computation. If you want trust guarantees, you pay for every operation in gas – but if you go off-chain for scalability or advanced logic, you lose those guarantees. Verifiable compute flips this paradigm: now, heavy computation can happen off-chain, but its results are cryptographically proven and anchored on-chain, preserving security and decentralization.
This isn’t just theoretical. EigenCloud’s recent mainnet alpha launch brings verifiable AI to the mass market with EigenAI and EigenCompute services, letting developers run expressive application logic in verifiable off-chain containers. As Delphi Digital puts it, these containers can perform heavy lifting off-chain while returning lightweight proofs that smart contracts can verify.
The Latest Breakthroughs: zkML, TEEs and Cross-Chain Proofs
The last year has seen a surge of innovation across multiple layers of the verifiable compute stack:
Breakthroughs in Verifiable Computing (2025 Edition)
-

Polyhedra’s zkPyTorch Compiler: Launched in March 2025, zkPyTorch transforms PyTorch AI models into zero-knowledge circuits, enabling cryptographic proofs of correct execution for machine learning. This breakthrough brings verifiable AI to decentralized applications, making ML computations provable and trustless.
-

Oasis Protocol’s ROFL Mainnet: In July 2025, Oasis Protocol Foundation launched ROFL, a mainnet framework for verifiable off-chain compute. ROFL leverages Trusted Execution Environments (TEEs) to perform complex computations privately and securely, then anchors verifiable results on-chain—ideal for AI and privacy-first dApps.
-
Phala Network’s TEE Verifier Network: Phala Network has integrated over 30,000 TEE devices, creating a robust verifier network for secure, privacy-preserving computation. This infrastructure is powering decentralized AI training and secure data processing with cryptographic proof guarantees.
-
Trusted Compute Units (TCUs): Introduced as a flexible framework, TCUs enable composable, interoperable verifiable computations across various technologies. DApps can offload heavy computation to trusted units and receive on-chain proofs, boosting scalability and efficiency.
-

V-ZOR Protocol: V-ZOR combines zero-knowledge proofs with quantum-grade randomness for secure, verifiable cross-blockchain communication. Its innovative reporter selection mechanism enhances the integrity of bridges and oracle networks.
-

Chainlink Automation 2.0: The latest update to Chainlink Automation brings verifiable compute to the mainstream. Developers can now offload on-chain tasks to cryptographically verified off-chain processes, reducing costs and increasing performance while maintaining trustless guarantees.
Polyhedra’s zkPyTorch compiler now lets PyTorch AI models generate zero-knowledge proofs about their execution (source). This means you could run a massive machine learning model off-chain and prove to anyone – without revealing your data or model weights – that it produced a specific result.
Oasis Protocol’s ROFL mainnet, launched July 2025, leverages Trusted Execution Environments (TEEs) for privacy-preserving offchain computation that remains verifiable when brought back on-chain (source). Meanwhile, Phala Network boasts over 30,000 TEE devices supporting secure multiparty computation for use cases like confidential AI training (source).
Flexible Trust Models: Moving Beyond “Trust But Verify”
The real magic happens when these technical advances are woven into new trust models tailored to different app needs:
- Trusted Compute Units (TCUs): These modular frameworks enable composable and interoperable computation across diverse tech stacks. Dapps can send jobs to TCUs and receive proofs that are easily verified on any chain.
- V-ZOR Protocol: By combining zero-knowledge proofs with quantum-grade randomness for reporter selection in cross-chain messaging, V-ZOR addresses both data integrity and bridge security challenges.
- Chainlink Automation 2.0: Chainlink’s upgrade brings verifiable compute to its automation platform so devs can reduce costs while maintaining crypto-grade guarantees (source).
This flexibility is crucial as decentralized infrastructure evolves to support more sophisticated apps – from agentic AI on Ethereum to privacy-preserving DeFi analytics across chains.
What’s striking about this new landscape is how it dissolves the old dichotomy between trust and scalability. In the past, developers had to pick: either keep everything on-chain for maximum trust but minimal throughput, or go off-chain and accept a leap of faith. Now, with verifiable compute, you can have both. Applications can scale to millions of users or process advanced AI logic without ever sacrificing auditability or decentralization.
This paradigm shift is already visible in projects like EigenCloud, which brings cloud-scale programmability to the blockchain world without compromising on cryptographic verifiability. By anchoring proofs of off-chain computation on-chain, EigenCloud ensures that even the most complex operations, from AI inference to cross-chain swaps, remain open to independent verification.
Real-World Impact: What Verifiable Compute Enables
The implications are huge for both users and builders. Here’s what’s now possible thanks to these advances in offchain proofs and flexible trust models:
Real-World Use Cases Unlocked by Verifiable Compute
-
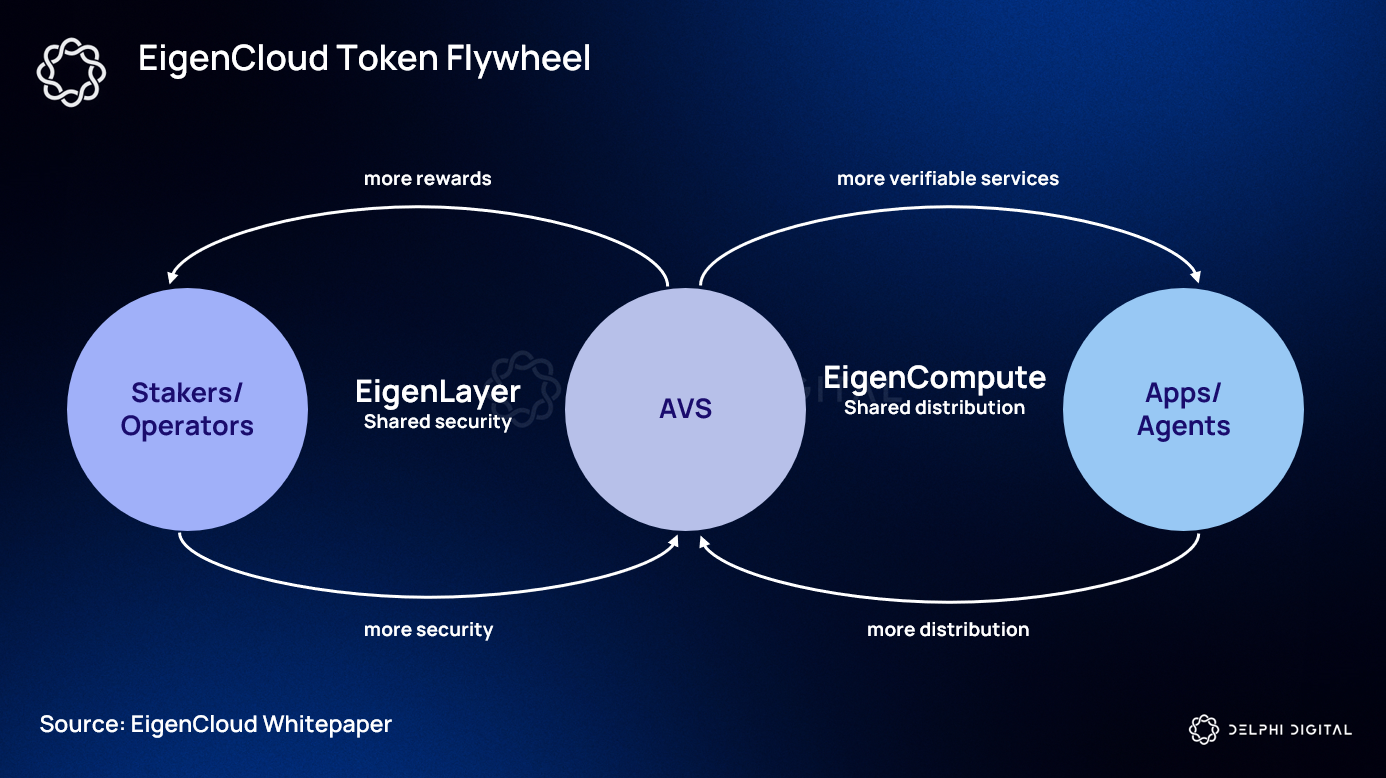
Scalable AI Agents on Ethereum: Platforms like EigenLayer and EigenCloud now enable agentic AI to run complex tasks off-chain, with cryptographic proofs ensuring results are trustworthy. This unlocks decentralized, verifiable AI-powered apps without congesting the blockchain.
-

Privacy-Preserving DeFi Analytics: Solutions such as Oasis Protocol’s ROFL and Phala Network use Trusted Execution Environments (TEEs) and zero-knowledge proofs to perform sensitive analytics off-chain. This allows DeFi platforms to offer advanced, privacy-focused analytics while keeping user data secure and computation verifiable.
-
Secure Cross-Chain Messaging: Protocols like V-ZOR and Chainlink Automation 2.0 use verifiable compute and zero-knowledge proofs to ensure that messages and data passed between blockchains are tamper-proof and independently auditable, reducing risks in cross-chain bridges and oracles.
-

Decentralized Gaming Logic: With tools like Polyhedra’s zkPyTorch compiler, game developers can run heavy computations (like AI NPCs or game logic) off-chain, then prove the results on-chain. This enables fair, scalable, and trustless gameplay in blockchain-based games.
Developers can finally implement rich business logic, think AI-powered trading bots or privacy-first healthcare apps, without worrying about blockchain bloat or opaque third-party computation. Users get ironclad guarantees that results weren’t tampered with behind closed doors. And investors gain confidence that protocol incentives are enforced by math, not just reputation.
The broader ecosystem benefits as well. With frameworks like TCUs and protocols like V-ZOR, interoperability barriers start to crumble. Cross-chain DAOs can coordinate actions with cryptographic assurance, while oracle networks become more robust against manipulation and censorship.
Challenges Ahead, and Why They’re Worth Tackling
No breakthrough comes without friction. The main hurdles now are performance overheads from proof generation (especially for zkML), developer tooling maturity, and the need for robust standards across chains and cloud providers. But the momentum is undeniable: as teams iterate on zero-knowledge compilers, TEE orchestration layers, and modular trust primitives, these pain points are gradually being sanded down.
If you want a front-row seat to this evolution, keep an eye on collaborations like EigenCloud’s partnership with Google Cloud or Oasis Protocol’s ongoing work with confidential AI applications. The modular blockchain stack is morphing into something more powerful than its parts, a global compute mesh where anyone can verify anything, anywhere.
The upshot? As verifiable compute matures from bleeding-edge research into mainstream infrastructure, it will unlock entirely new classes of decentralized applications, many we haven’t even dreamed up yet. For now, one thing is clear: trust in crypto infra is no longer just about consensus, it’s about proof at every layer.






